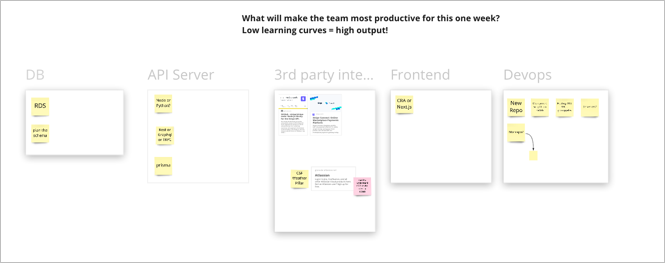
Prefer Boring Technologies
Boring technology prevents surprises.
Surprises slow down development. Use boring technology unless overridden by another constraint.
I tend to get a lot done when I’m excited about the newness of something. I feel the excitement and get into “the zone” a lot easier when I’m trying out new tech. When it’s time to build a project for maintainability and longevity it’s best to have already gotten that out of one’s system. Know the tech that you like using the best and are most familiar with. Learn new things so that when it’s time to build something serious you have the knowledge base so fewer things will be surprises. Adopt very few “surprising” things. Surprising other developers (and future you) is a bad thing. It causes frustration and confusion. People will make assumptions about tools and libraries instead of reading documentation. So chose tools and languages and libraries that are widely understood and easy to learn about. Try not to implement things in surprising and clever ways.
Use well-maintained technology.
If the tool is simple and just “finished” then evidence of frequent maintenance releases isn’t really a problem.
Normally I want to see that maintainers of a project are putting out minor patches pretty frequently. Hopefully they are updating their dependencies and responding to support requests and merging pull requests. If the tool is very niche, and if it doesn’t have any dependencies to update then that’s actually better because there is less for the library author to maintain. But generally I want to see that some releases have happened in the last 6 months and issues do get answers or comments sometimes.
The biggest risk we are trying to mitigate with checking maintenance frequency is, If you run someone else’s code, and it runs in a dynamic context where we see frequent new and emerging interactions with other technologies, or where users and clients will be calling it directly (like an API server), then it had better be frequently updated and maintained and scanned for security vulnerabilities.